Introducing Chomp Scan
Today I am introducing Chomp Scan, a pipeline of tools used to run various reconnaissance tools helpful for bug bounty hunting and penetration testing.
Why Chomp Scan?
The more I’ve gotten into bug bounty hunting, the more I’ve found times where managing all the different scanning tools, their flags, wordlists, and output directories becomes a chore. Recon is a vital aspect of bug hunting and penetration testing, but it’s also largely repetitive and tool-based, which makes it ripe for automation. I found I was contantly running the same tools with similar flags over and over, and frequently in the same order. That’s where Chomp Scan comes in.
I’ve written it so that all tool output is contained in a time-stamped directory, based on the target domain. This way it’s easy to go back and find certain outputs or grep for specific strings. As a pentester or bounty hunter, familiarity with your tools is essential, so I include all the flags, arguments, parameters, and wordlists that are being used with each command. If you need to make a change or tweak a flag, the code is (hopefully) commented well enough to make it easy to do.
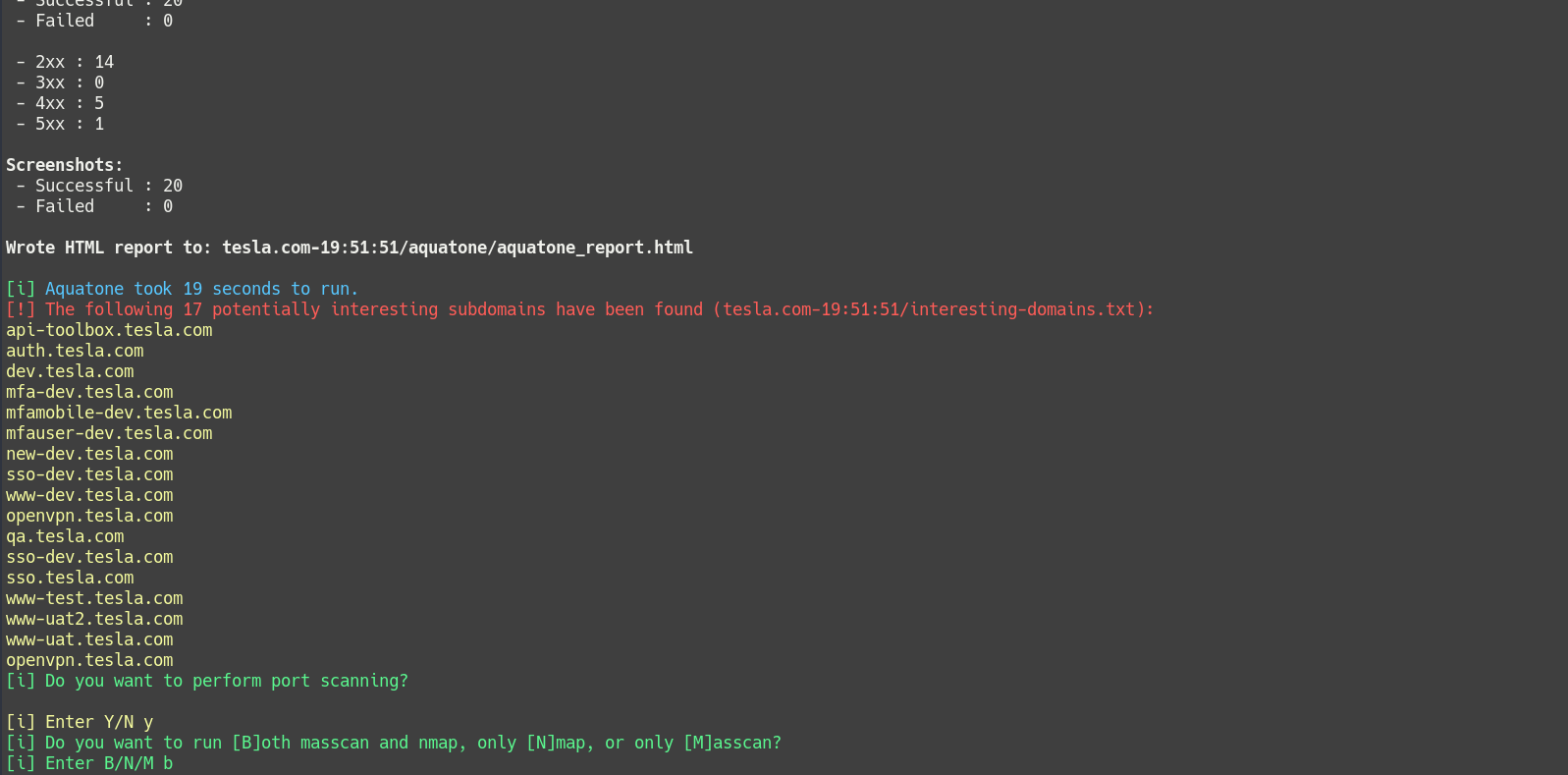
A neat feature I’ve included is a list of words called interesting.txt. It contains a lot of words and subdomain fragments that are likely to be of interest to a pentester or bug hunter, such as test, dev, uat, internal, etc. Whenever a domain is discovered that contains one of these interesting words, it is flagged, displayed in the console, and added to a list. That list can then be focused on by later scanning stages, allowing you to identify and spend your valuable time on the most high value targets. Of course interesting.txt is customizable, so if you have a specific keyword or subdomain you’re looking for, you can add it.
Scanning Phases
Chomp Scan has 4 different phases of scanning. Each utilizes one or more tools, and can optionally be skipped for a shorter total scan runtime.
- Subdomain Discovery (3 different sized wordlists)
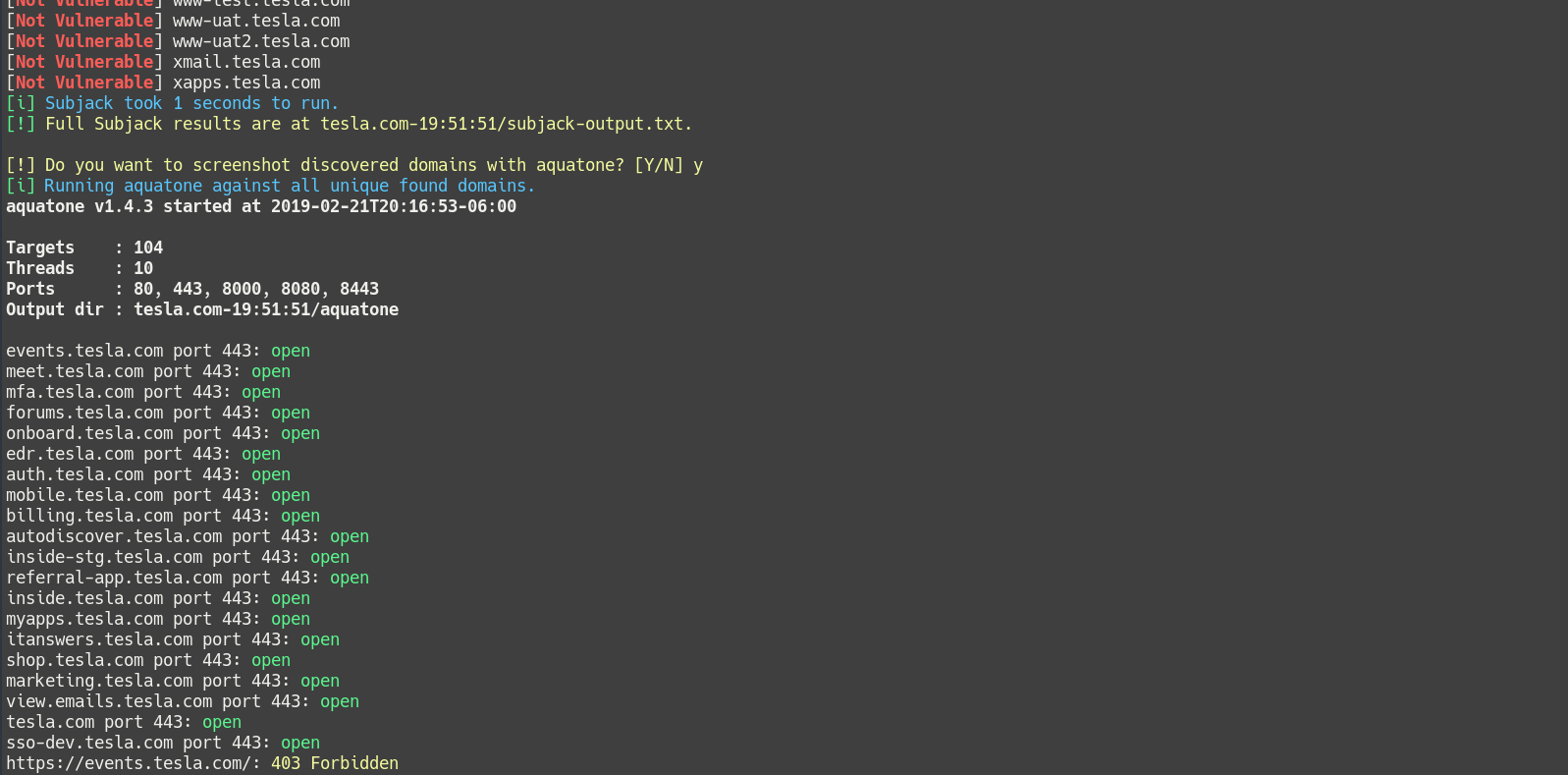
- Screenshots
- Port Scanning
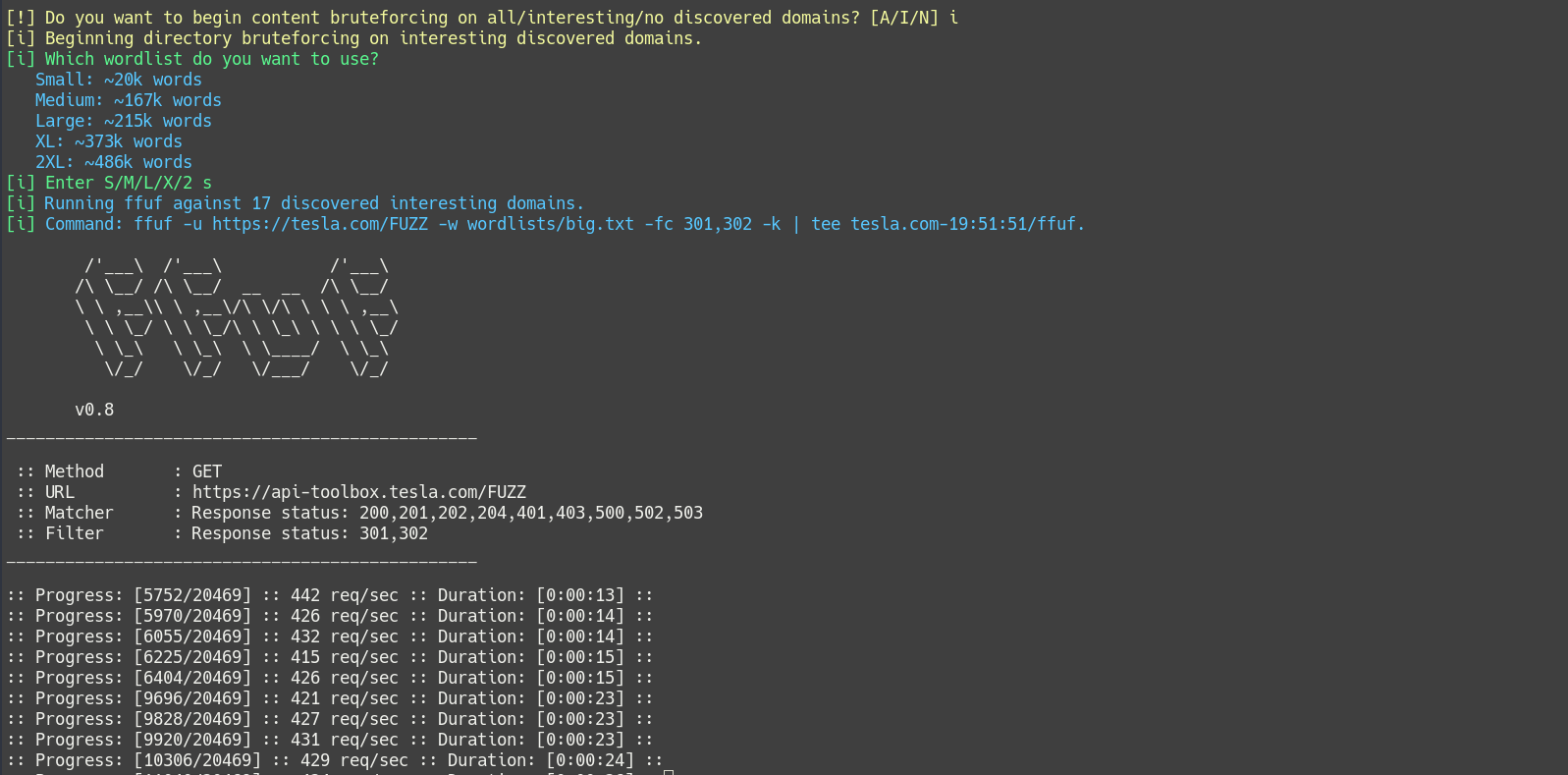
- Content Discovery (4 different sized wordlists)
In The Future
Chomp Scan is still in active development, as I use it myself for bug hunting, so I intend to continue adding new features and tools as I come across them. New tool suggestions, feedback, and pull requests are all welcomed. Here is a short list of potential additions I’m considering:
- A non-interactive mode, where certain defaults are selected so the scan can be run and forget
- Adding a config file, for more granular customization of tools and parameters
- A possible Python re-write, with a pure CLI mode (and maybe a Go re-write after that!)
- The generation of an HTML report, similar to what aquatone provides
Tools
Chomp Scan depends on the following list of tools. Several are available in the default Kali Linux repos, and most are otherwise simple to install, especially if you already have a Go installation.
- sublist3r
- masscan
- nmap
- nikto
- gobuster
- whatweb
- chromium
- dnscan
- altdns
- bfac
- massdns
- subfinder
- subjack
- ffuf
- aquatone
How To Get It
Visit the Chomp Scan Github repository for download and installation instructions.